Trucking Industry Confronts Growing Cyber Threats
[Part 2 of 3] Amid rising cyber threats, the trucking industry strengthens defenses against hackers targeting critical transportation infrastructure, with experts rallying to secure the nation's supply chain from digital attacks. Part 2 of 3.

This article is the second installment in a three-part series exploring the trucking industry's urgent need to adopt more robust cybersecurity measures.
By Alan Schmadtke, for The Inside Lane
A decade ago, Urban Jonson sat in a Las Vegas hotel ballroom and listened to a pair of excited web developers tell an enthralled crowd how they had recently hacked the computer of a Jeep.
The possibilities that they had opened up, the developers explained, were boundless.
That night Jonson, a cybersecurity expert and consultant within the trucking industry, huddled with a colleague in a nearby bar and, based on what they’d heard that day, sketched out the computer vulnerabilities of a fleet truck.
“We were both terrified,” said Jonson. “I don’t care about passenger cars, but I care a lot about trucks. . . . We had work to do.”
He was concerned about an industry that the U.S. Census Bureau says is responsible for more than 70% of all goods shipped each year in the United States. It was ripe for the wrecking.
For Jonson, that day was a pivot point. He was determined to help trucks — and truckers, trucking companies and the national transportation system — fight back.
He took his crumpled napkin home, and it was the foundation for a white paper published in 2019 about the cyber vulnerabilities of the American trucking business.
“The industry has done a lot since then,” Jonson said. “But it doesn’t end. There’s always a ‘next thing.’”
Today’s trucks are hackable 'offices on wheels'
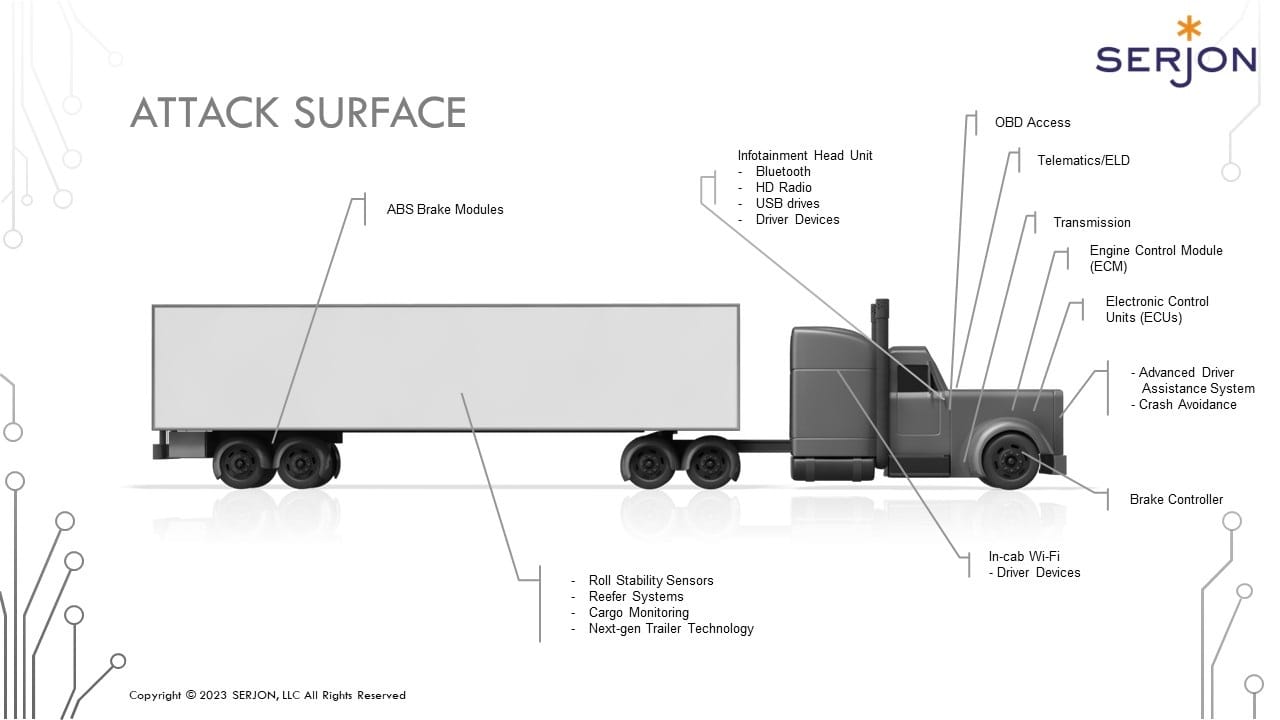
That there are computers in cars — and trucks — is hardly news. But most people don’t realize what they control and what they do. Trucks have six to eight systems that generate and share data about the vehicle, status, performance, location, cameras and other parts of the truck.
The security integrity of each of those systems differs. They’re designed and built by different original equipment manufacturers (OEMs).
Like most computer systems, they require periodic upgrades and patches. Best practice dictates that, from birth to death, systems get tested for security.
“The truck today is much different than the truck [of] 15 years ago. The truck today is an office on wheels,” Joe Ohr, chief operating officer for the National Motor Freight Traffic Association (NMFTA) told The Inside Lane.
“It’s got Wi-Fi. It’s got tablets. ELDs [electronic logging devices]. It’s got phones. It’s got Bluetooth. It’s got all these connection points that somebody could come in and access and do something.”
NMFTA is one of a shortlist of groups, including Homeland Security, that does research and tests parts and systems for potential problems. When something fails, it gets the word out, because many parts and systems are off-the-shelf products, one that hundreds or thousands of fleet operators and trucks across the country rely on.
If a truck or trucking company gets hacked, odds are the criminal isn’t someone working on one laptop from a couch in a basement.
“It’s probably a nation-state, China or Russia,” Ohr said.
Cyberattacks on fleets are low - for now
Despite the low incidence of cyberattacks on trucks, the risk persists in this increasingly digital industry.
“It’s not easy to attack a truck. If it were easy, anyone who understands computer programming could do it,” said Hossein Shirazi, a computer engineer and professor at San Diego State University who studied, and recreated, truck cyber attacks as part of his research.
“At the same time, wherever there is a network, there is a possibility for an attack.”
The trucking industry represents only 5% of cyber security attack targets in the U.S., according to FBI data. Trucking professionals might find some comfort in knowing that hackers often prioritize more lucrative sectors such as banking, insurance, healthcare, utilities, and key government entities like the Social Security Administration and the IRS.
“They have technology and networks that they’re connected to. Those things can be breached,” FBI cyber security analyst Trina Martin said about trucks. “And it’s not just a system vulnerability. It’s also human vulnerability.”
Said Jonson: “It’s a matter of when, not if. I mean, we’ve already seen if.”
The motive behind fleet cyber attacks
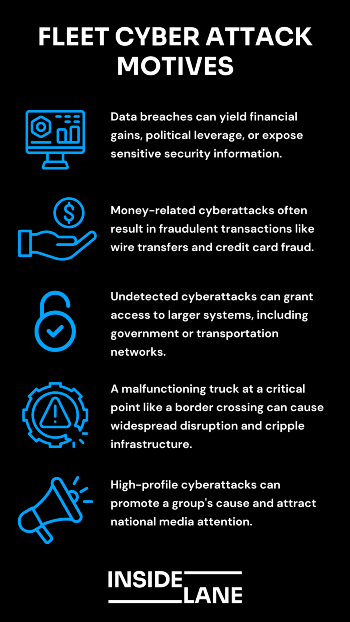
Why attack a truck? Or a trucking business? Most of the reasons involve money, publicity or disruption.
Motive depends on the attacker(s), some of whom embrace an ideology, some of whom operate at the discretion of a foreign government. Others simply want to get rich quick.
Cybersecurity experts say the five most common reasons are:
- Data: This can lead to financial profit, political leverage or information related to personnel or security. A trucking company with several well-heeled clients can surrender valuable information.
- Money: Breaches can lead to fake wire transfers, payments, credit card transactions, etc.
- Access: If undetected, an attack can provide an entryway into bigger systems, such as communications with government agencies or transportation agencies.
- Disruption: One failed truck at a key checkpoint (think border crossing) or road can create widespread havoc. Crippling infrastructure is also an aim.
- Publicity: A group might further its political, cultural or environmental cause with a successful high-profile attack, at least in the short term. A successful attack can generate national media attention.
“It’s only getting worse with [better] technology and AI,” Martin said. “We look at these and think, ‘Oh, these are going to make my life easier.’ But the criminals are thinking the same thing, but for nefarious reasons. ‘How can I use AI to increase my tactics?’"
Colorado State students get ahead of hackers
One way the trucking industry tries to stay ahead of the bad actors is to build a better hacker. That’s where the college students come in.
Colorado State University has students and graduate students who study, research, test and write about vehicle and heavy truck computer systems. About 380 graduate students work in a cyber lab with doctoral students and faculty.
Once a year, many of them gather in Michigan for an annual CyberTruck Challenge, a week of learning and collaboration between students and industry leaders, manufacturers and professionals. The event highlights a growing talent pool from which trucking companies — and transportation-related government agencies — can find smart people who want to stay one step ahead of the adversary. Counter-hackers, if you will.
“It’s hands-on. It’s not theory,” said Jake Jepson, a second-year graduate student at Colorado State. “You get to see how it matters in the real world.”

Jonson, Martin and other cybersecurity experts know about a handful of bad actors, almost all foreign, who have attacked trucks or trucking businesses over the past decade. They include:
- FIN7, a financially motivated Russian threat group that likes to target U.S. industries, especially those active in point-of-sale transactions.
- Leviathan, a Chinese-state-sponsored cyber espionage group that goes after transportation, defense, engineering, government and other U.S. sectors.
- Earth Centaur, an unaffiliated gang operating in Asia, has attacked transportation companies and government agencies related to transportation. It was formerly known as Topic Trooper.
- APT29 (Fancy Bear), a Russian-state group linked to the GRU, has hit Microsoft and carried out multiple high-profile attacks over the past decade, though not as much in the transportation sector.
- TA2541, a loosely affiliated cluster of hackers who have targeted the aviation and transportation sectors since 2017.
These groups and others use techniques that have proven successful. They use remote access tools (RATs), valid accounts and poor log-in protocols to gain system access.
They also rely on phishing expeditions, emails with links and attachments that, when clicked on, make a computer (and a network) vulnerable to receiving illicit scripts, code and executable files.
They prefer to attack at scale — make a splash and deliver impact. That means not one truck but many, or else the company’s network. However, if that’s not possible, they’ll attack one truck and work their way backward.
Truck cyber attacks trending upward
FBI data shows 35 reported ransomware attacks on trucking companies over the past nine years. But there were 34 data breaches in 2023-24 — and already 25 phishing crimes this year.
What mostly concerns industry insiders, law enforcement and U.S. transportation officials is the increasing number of incidents. Unfortunately for them, cyberattacks are a growing business.
And everyone speaks quietly about a subject no one wants to ponder: when is the 'Big One' coming, and what will it be?
Martin, who has a Naval intelligence background besides her 13 years with the FBI, works closely with the transportation, oil and gas, energy and medical sectors to get the word out about the bad actors and to promote preventative cybersecurity actions.
The good news for the trucking industry is that nearly 85% of the commercial trucks on American highways are owned or operated by smaller businesses, companies with one to 25 trucks.
“You’re not going to shut down the transportation system if you hit 15 trucks,” Jonson said. “You’ve got to do a lot of work to hit enough trucks to cripple the system. But there are people out there who are willing to do it.”
Thank you for reading the second installment of The Inside Lane's three-part series on cybersecurity in the trucking industry.
Part 1 takes a look at the alarming trend of cyberattacks in trucking, a sector integral to the U.S. economy. Industry experts highlight the critical need for advanced cyber defenses. Read it here.
Part 3 will provide strategies, tactics, and tips to help small and mid-sized trucking companies fortify their defenses against cyber threats. Read it here.
Have a question or comment about this article? Email Bianca Prieto at editor@theinsidelane.co
Not yet a subscriber? Join here for free.





Comments ()